Now lets try to integrate our keycloak server with simple spring boot application and secure our url. In this exercise we will try to expose two url one public and one private and will try to protect our private url using keycloak server as an IDP.
For this exercise we will follow below step sequence wise
1- create client in keycloak
2- create role in keycloak
3- create user in keycloak
4- Create a spring boot application
5- finally integrate keycloak in springboot application using confi
Note here we are doing everyting in default realm i.e. Master for better use do not touch with default realm better to create your own using below screen.

But as said we are doing this POC on Master realm.
Lets do first step
1- create client in keycloak
Please follow below step religiously. We are using STS for the same.
In this exercise we are using OpenID connectore protocol and keycloak spring boot adapter (This is openid connector adapter).
First open the keycloak admin console and create new client.


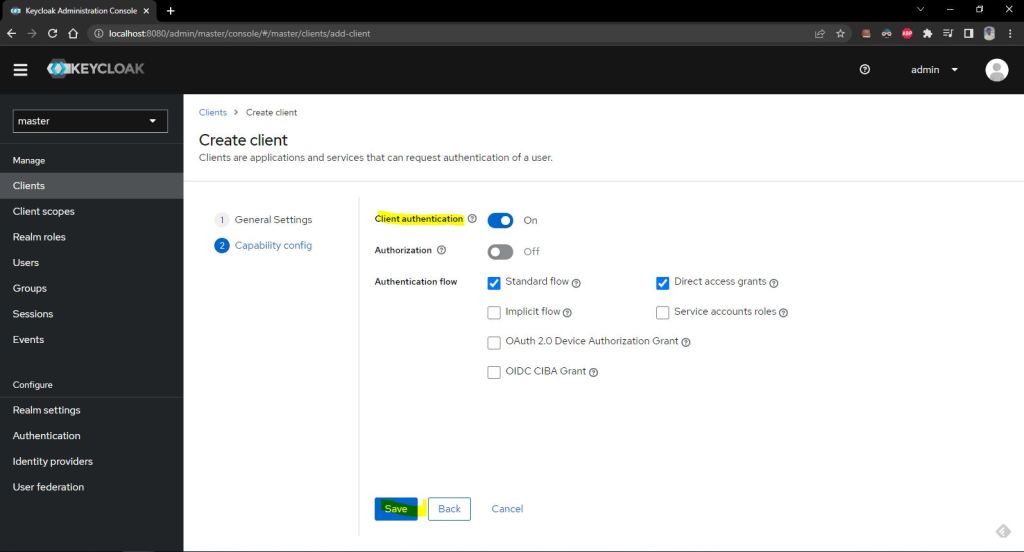

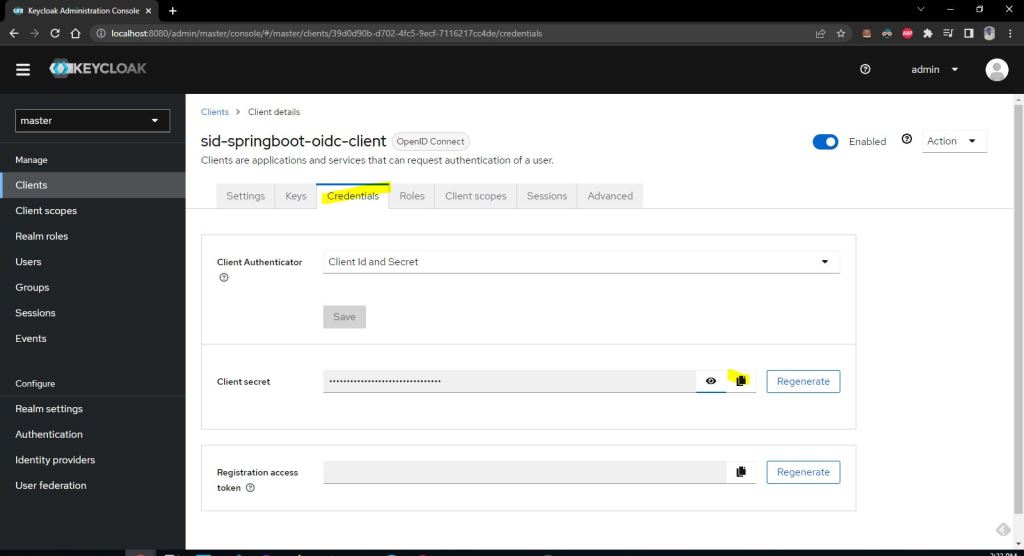
Now get the client secret from client credential
Now lets create a new role
2- create role in keycloak


3- create user in keycloak
Now we will assgin the role created in step 2 to a new user in this step 3.


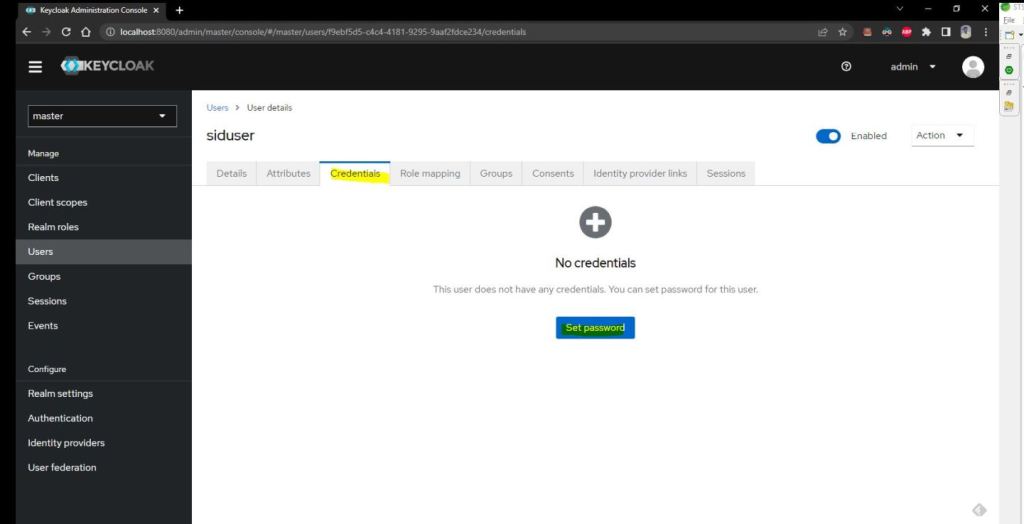
Now lets create the credential for this new created siduser using below screen



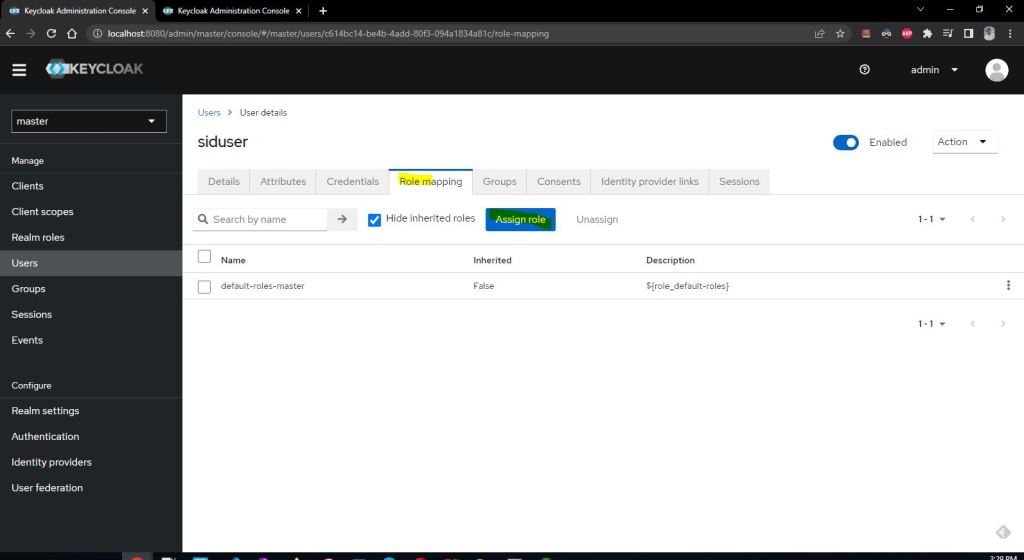
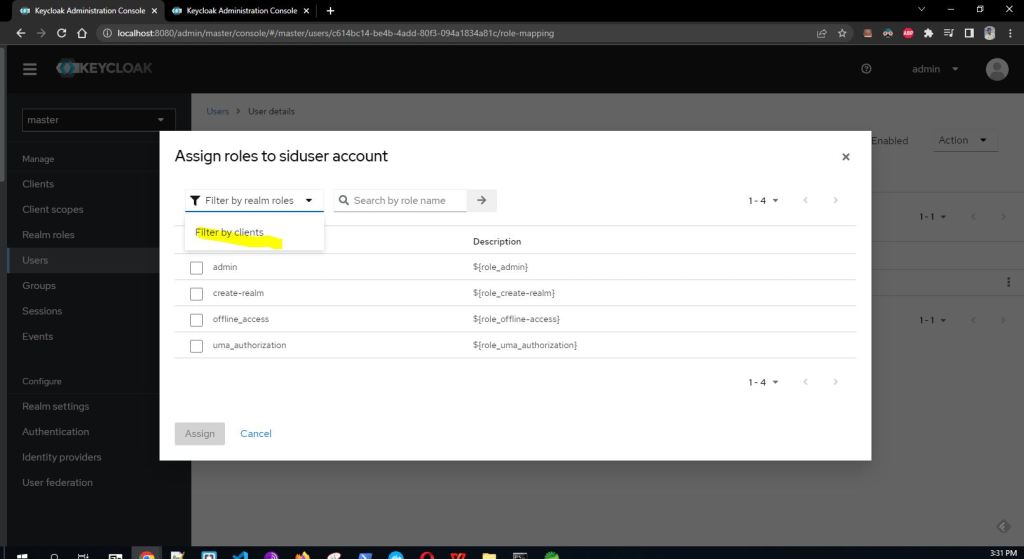
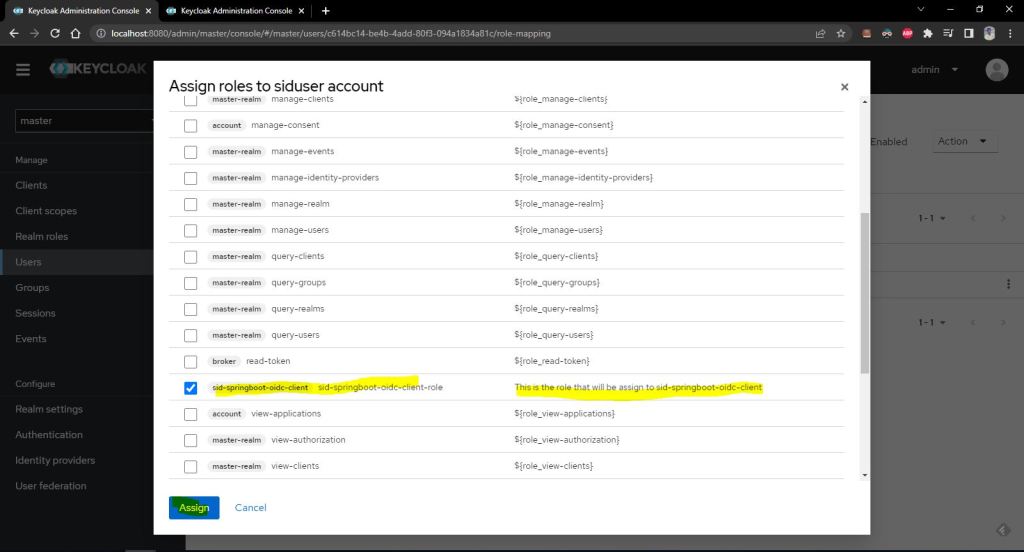
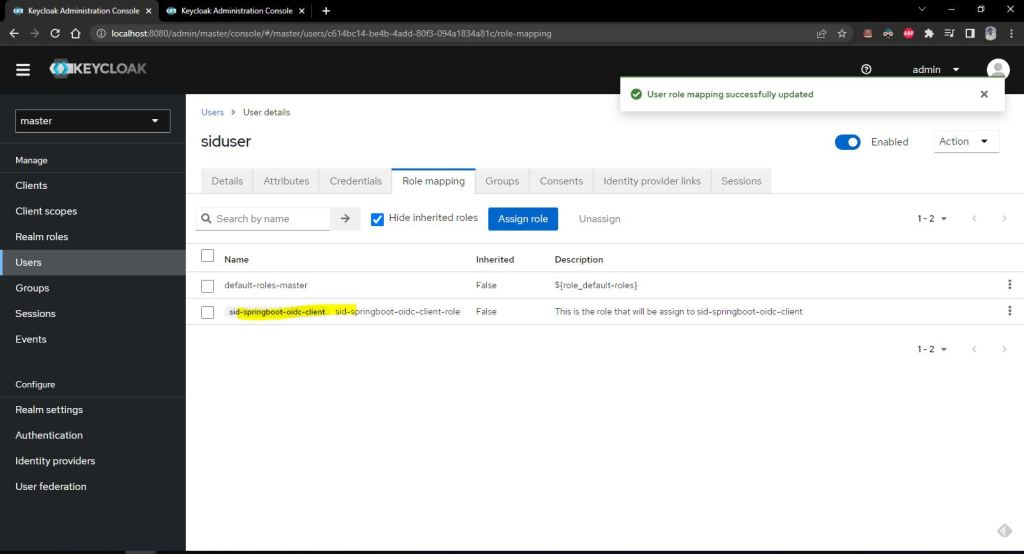
Now lets assign our created role to this user.

4- Create a spring boot application
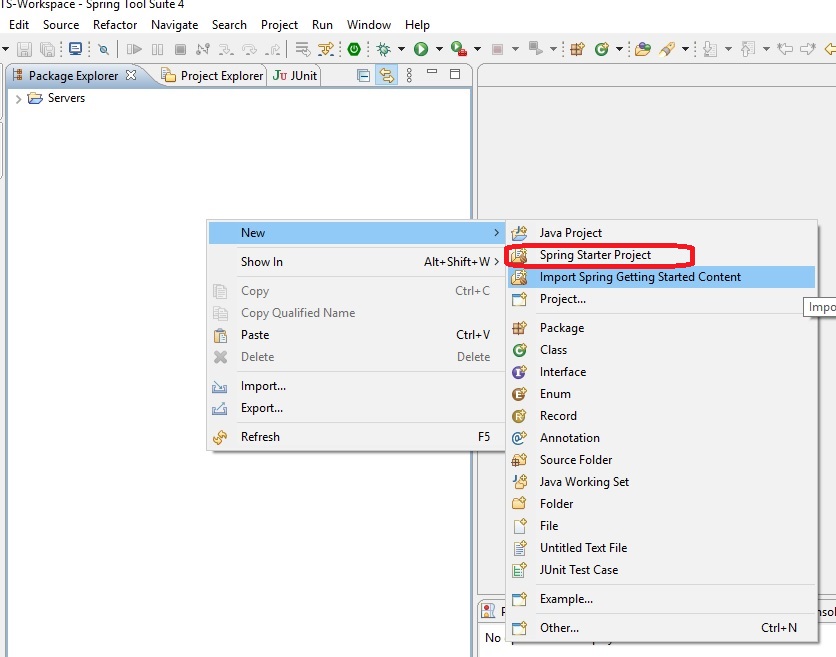
Now lets create the springboot application as below
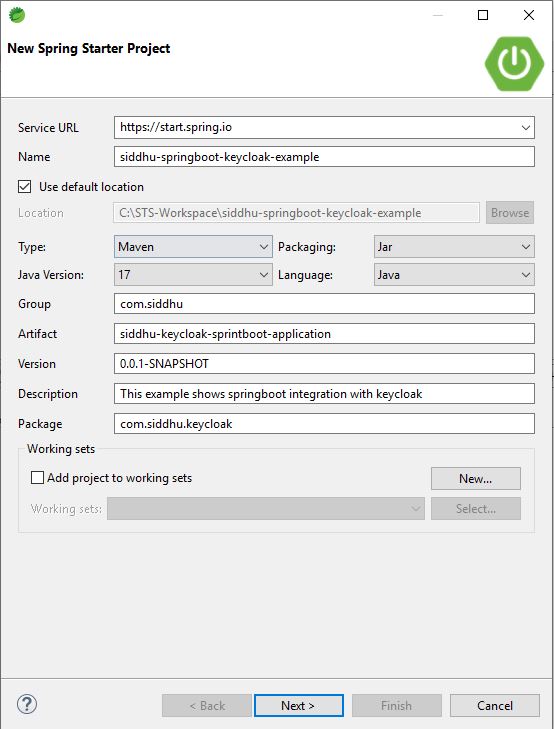

1 2 | https://start.spring.io/starter.zip?name=siddhu-springboot-keycloak-example&groupId=com.siddhu&artifactId=siddhu-keycloak-sprintboot-application&version=0.0.1-SNAPSHOT&description=This+example+shows+springboot+integration+with+keycloak&packageName=com.siddhu.keycloak&type=maven-project&packaging=jar&javaVersion=11&language=java&bootVersion=3.0.0&dependencies=web |

Now add following maven dependencies in pom.xml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | <dependency> <groupId>org.keycloak</groupId> <artifactId>keycloak-spring-boot-starter</artifactId> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> </dependency><dependencyManagement> <dependencies> <dependency> <groupId>org.keycloak.bom</groupId> <artifactId>keycloak-adapter-bom</artifactId> <version>20.0.2</version> <type>pom</type> <scope>import</scope> </dependency> </dependencies> </dependencyManagement> |
now lets try to add controller in spring boot so that it can display particular output for given url mapping.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 | package com.siddhu.keycloak;import java.util.Date;import org.springframework.web.bind.annotation.GetMapping;import org.springframework.web.bind.annotation.RequestMapping;import org.springframework.web.bind.annotation.RestController;import jakarta.servlet.http.HttpServletRequest;@RestController@RequestMapping("/")public class SiddhuSpribgbootKeycloakController { @GetMapping("/public") public String getPublicResource(HttpServletRequest httpServletRequest) { return "This is public resource" + new Date().toString(); } @GetMapping("/private") public String getPrivateResource(HttpServletRequest httpServletRequest) { return "This is private resource" + new Date().toString(); }} |

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | Now lets make configurarion server.port = 8081keycloak.enabled = truekeycloak.realm = masterkeycloak.auth-server-url = http://localhost:8080keycloak.ssl-required = nonekeycloak.resource = sid-springboot-oidc-clientkeycloak.credentials.secret = 7tJTeA03XdQQx2o4XievmkjL35DGdNmakeycloak.use-resource-role-mappings = truekeycloak.securityConstraints[0].securityCollections[0].patterns[0] = /private/*keycloak.securityConstraints[0].authRoles[0] = sid-springboot-oidc-client-role |
Now lets run our application and see if our springboot application is now secure with Keycloak
when you hit http://localhost:8081/public you will be able to see belwo screen

now try to hit private url



Note:- You can download the code from the belwo url
https://github.com/shdhumale/siddhu-springboot-keycloak-example
If you want to have a consent base login to the user you can do with the helpf following configuration.
Go to Client tab and select you created client in keycloak admin console and update as shown in the below screen
Once done when the user hit the protected url he will get below screen on the browser




No comments:
Post a Comment